Using OWASP ZAP with iOS
Introduction
In this post I’m going to go through how to intercept http and https traffic from an iOS device using OWASP ZAP. I have found this to be very handy when debugging web and iOS applications from the device. The version of ZAP that I am using is 2.4.3 and iOS is 9.3.
Set up HTTP Proxy
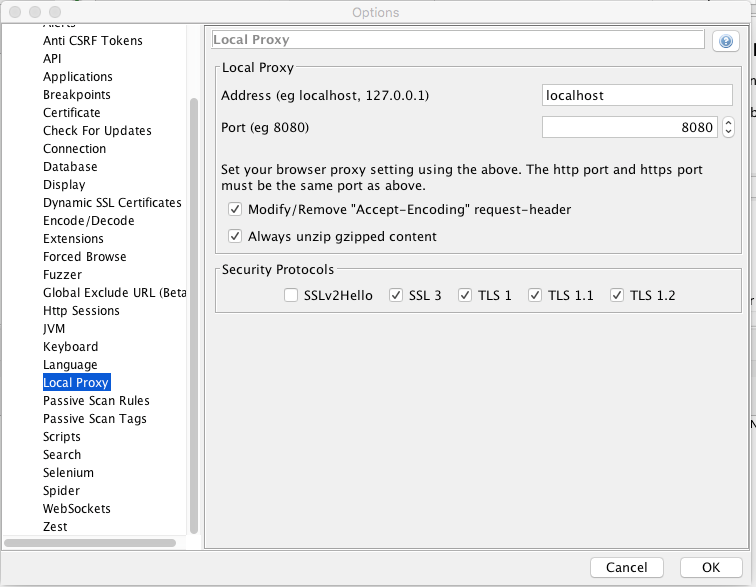
First lets open the local proxy settings in zap. Set the ip and port address that you want.
To allow your iOS device to go through zap, we need to change the wifi settings to do so.
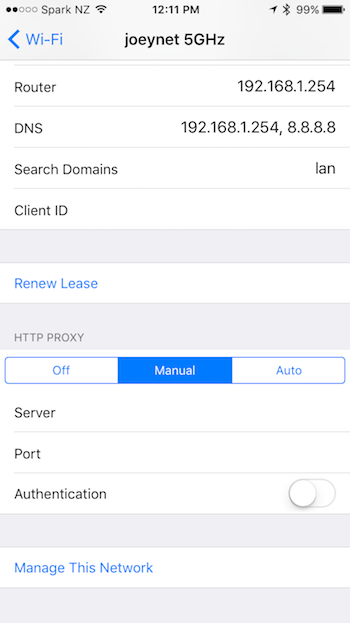
Select Manual entry, and enter the IP address and port number that you have zap running on.
Intercepting traffic
Now that the proxy is up and running, navigate to a website (example.com) from safari.
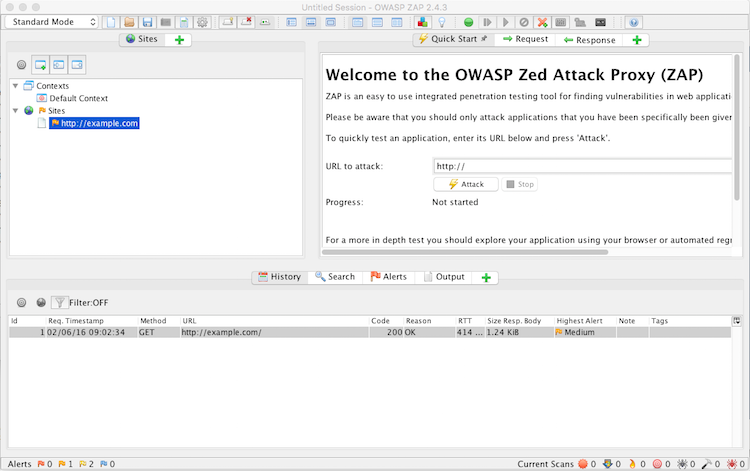
Over in zap you can see the history of your requests.
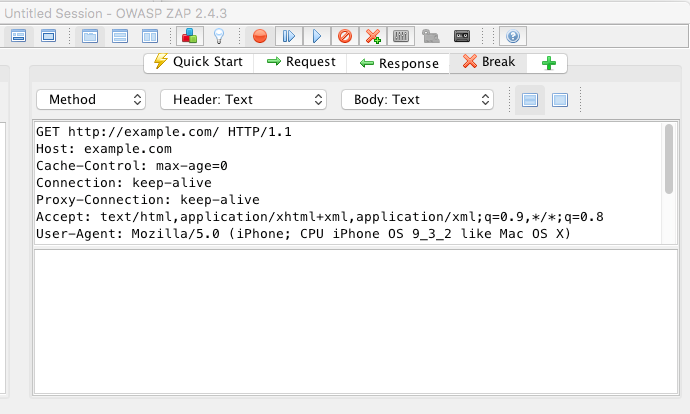
From the Tools menu you set to break on request and break on response. This will halt the traffic to/from the browser.
Request
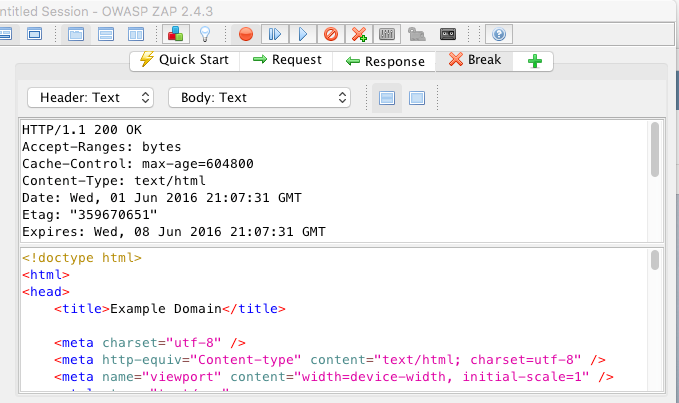
Response
Changing Request/Response
Viewing the traffic is nice, manipulating the traffic is even better. Change the heading from Example Domain to HACKED domain.
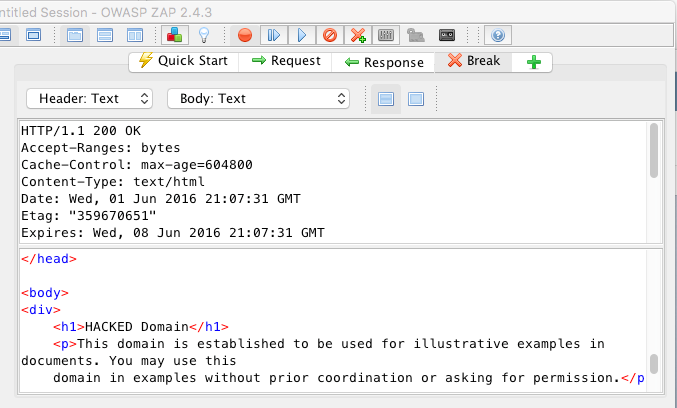
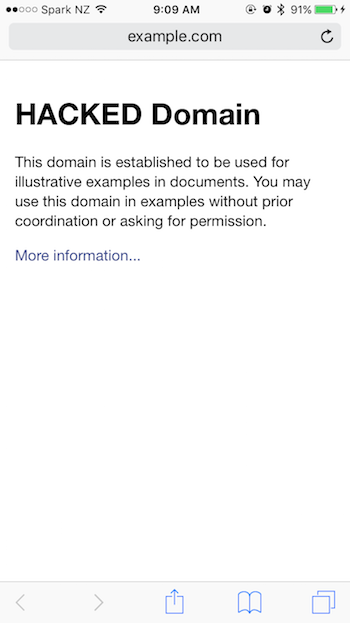
View the manipulated result on the device.
Dealing with encrypted traffic
Installing the root CA
To intercept the traffic on an encrypted link we must install a trusted root certificate. This will allow ZAP to encrypt and decrypt the traffic as it passes through.
Under the Tools -> Options… menu item we can find the Dynamic SSL Certificates section. From there we can generate and save the certificate to disk.
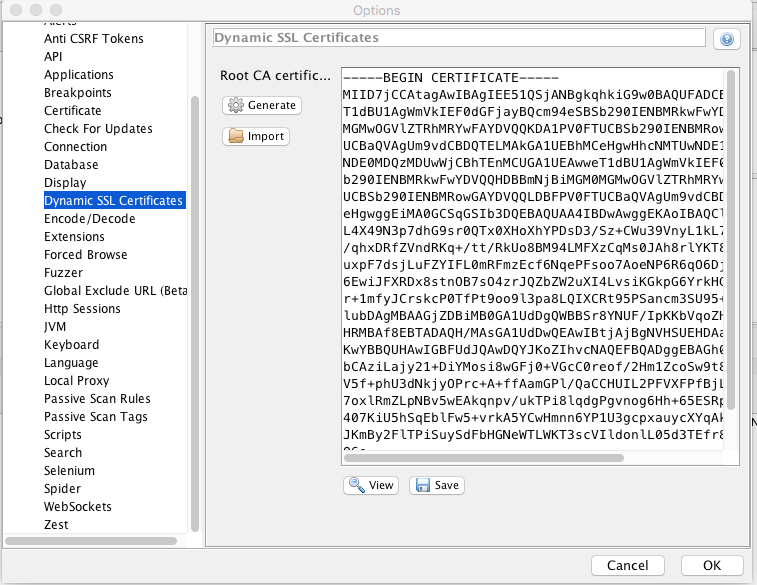
I have found the easiest way to transfer the certificate to the iOS device is to email it to an account you have on the device.
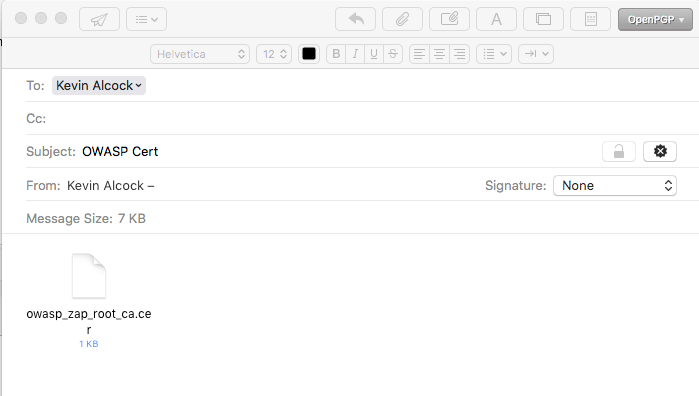
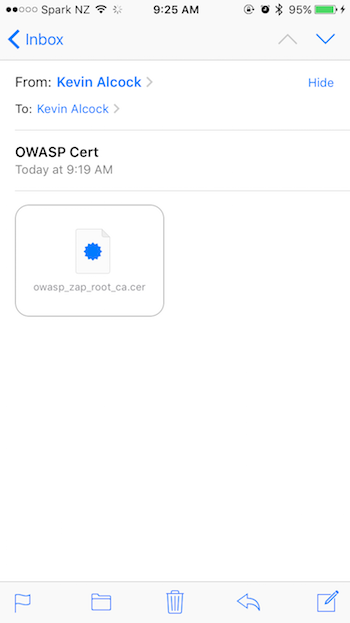
To install the certificate, touch the owasp_zap_root_ca.cer file. This will bring up the profile installer.
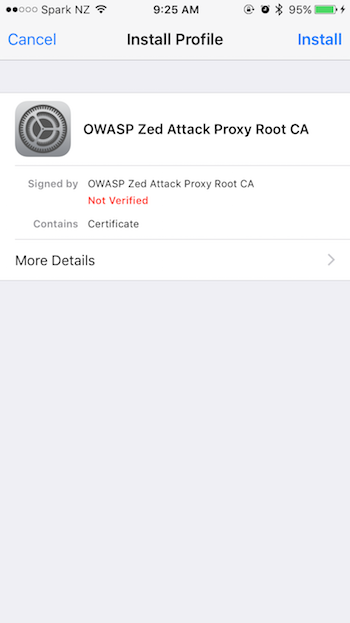
Press install
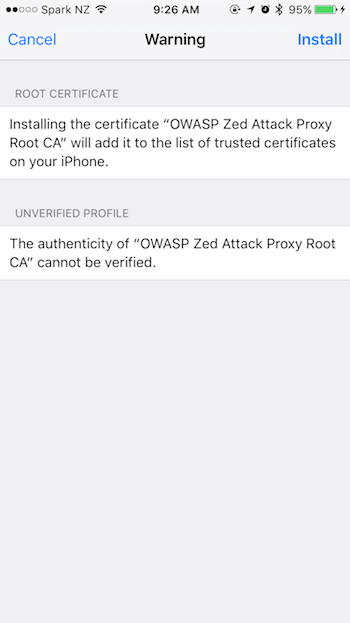
Press install
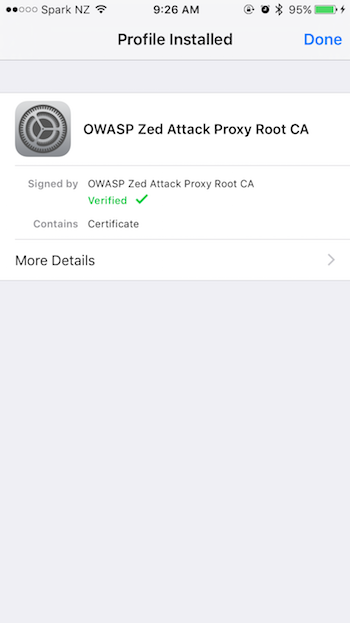
Viewing Encrypted Traffic
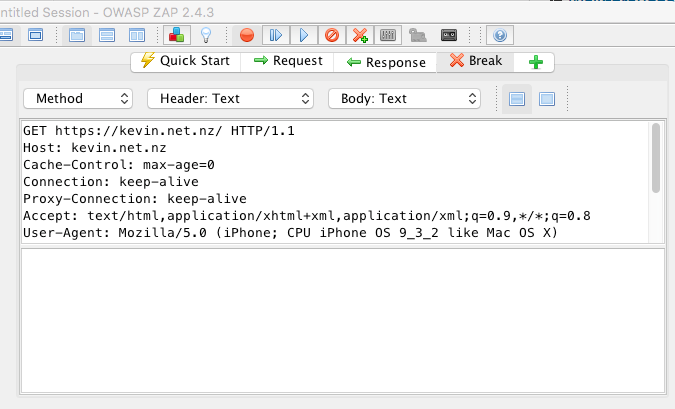
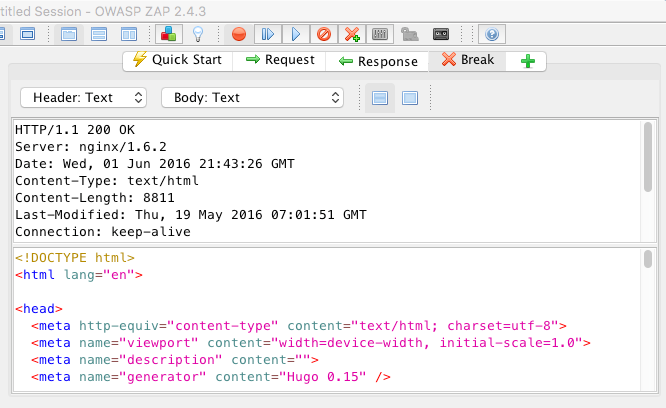
Viewing the encrypted traffic is just like before when we viewed the cleartext traffic. This time point your browser at a HTTPS site and then view the request and the response.
Request
Response
And Applications
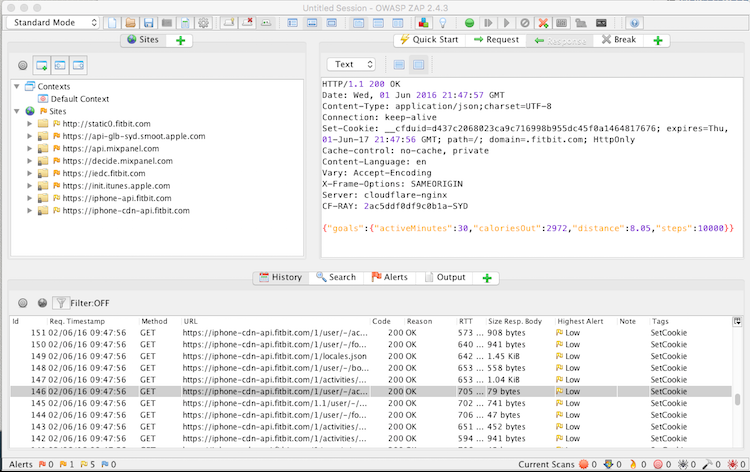
Up until now we have been looking at traffic generated via safari. You can also look at traffic sent via applications. Below is an example of traffic between the FitBit App and their server.